 |
| Image by HACKERHELD |
Nowadays data breaches are common and that is affecting billions of people all over the world. Countless email account compromised every year due to these data breaches and cybercriminals use them to send out fraudulent messages to your contacts or to steal any financial or personal information you’ve sent in past email messages. So this overview shows you how you can identify the company’s hacked email addresses or your own e-mail address using the HIBP transform and Maltego.
What is HIBP (Have I Been Pwned)?
HIBP (Have I been pwned) is a transform & website that allows internet users to search beyond many data breaches to check if their E-mail addresses have been compromised. It analyzes many database dumps and pastes that have details about maybe billions of compromised accounts. Users can also sign up to get notification if their E-mail address appears in the future dumps.
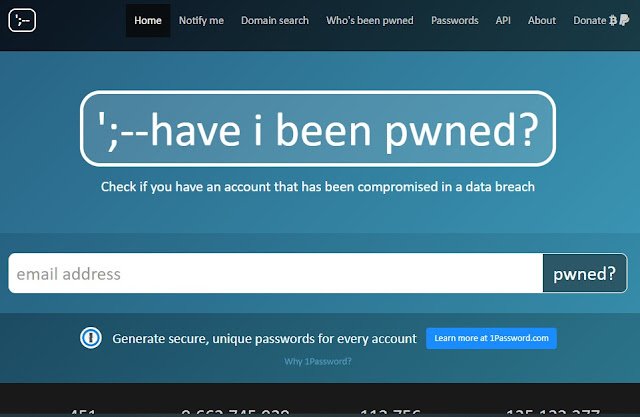
- To check the E-mail address ( Click Here ).
- After that enter an email address in the search bar and click enter.
 |
| Image by hackerheld |
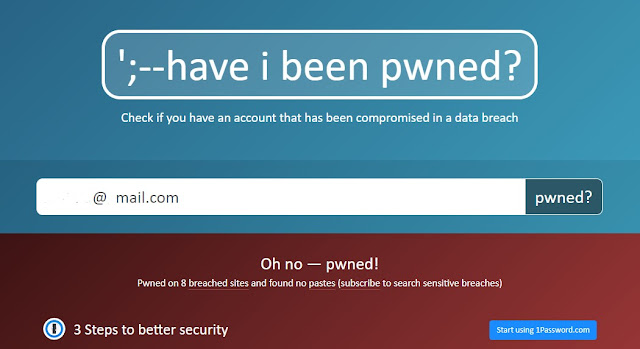
- Then wait for seconds or minutes depends on your network connection, to see your search results.
 |
| Image by hackerheld |
The "Have I Been Pwned" web version allows only to check a single email at a time but Maltego transforms to run the query allows us to search for many email addresses in one click and show data related to compromised accounts, email addresses, passwords, locations, and other personal information. So that's why to identify target company email addresses that may be vulnerable from third-party breaches we use maltego.
What is Maltego?
Maltego is an open-source intelligence (OSINT) and graphical link analysis tool that is used to find connections between pieces of information from different sources located on the Internet. The graphs permit you to easily build connections between information like name, domains, email organizational structure, documents, etc. it uses the idea of transforms to automate the operation of querying different data sources. Then this information is displayed on a node-based graph suited for performing link analysis that helps in gathering information for investigative tasks.
There are four versions of the Maltego client which is:-
- Maltego CE:- free, non-commercial use.
- Maltego Classic:- paid commercial use.
- Maltego XL:- paid commercial use.
- Maltego CaseFile:- free, commercial, no Transform.
Maltego is a Java application that so it can run on Windows, Mac, and Linux and is available in many OSINT Linux distros like Kali. it allows users to create graphs that will help you put the pieces together step-by-step in an intuitive point-and-click logic.
Install Maltego
- To install Maltego, you'll must have installed java on your machine. If you're using Kali Linux, It comes pre-installed on it so no need to get in the installation steps but if you are using any other Operating System you can simply download Maltego from its official website. To download ( click here )
- Then You need to make an account on Paterva to use the Community version. To create an account ( click here )
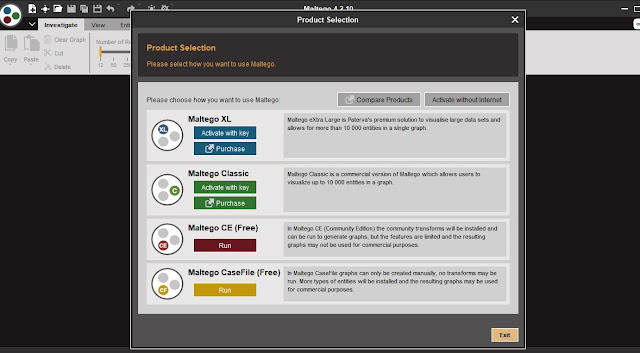
- Once you install Maltego, You need to open the application. It will ask which version you want to use, we will use (Maltego CE free) Community version, and then we need to log in to use the tool.
 |
| Image by hackerheld |
Install the HaveIBeenPwned Transform
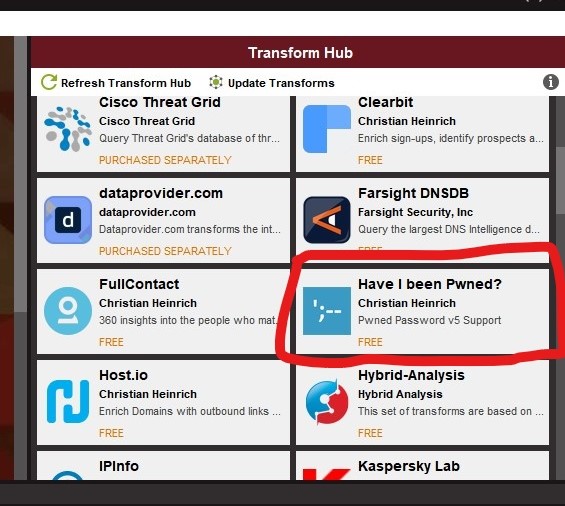
- Once you log in, you will get the main page of the transform hub. Here, you can install various free and paid transforms to enrich the data you find. We need to install "haveibeenpwned" transform luckily its free.
 |
| Image by hackerheld |
Create a New Graph
- When the "haveibeenpwned" transform successfully installed, you can click on the document icon to create a new graph that is on the top-left corner. This is where we will begin our investigation.
 |
| Image by hackerheld |
Scraping Email Addresses From An Organization
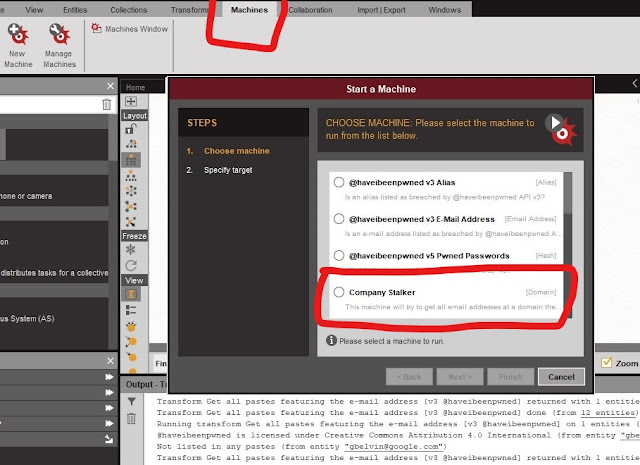
- After creating a new graph. we use the Company Stalker machine. we need to simply click on - machine > run machine > select company stalker > enter the company domain name > click on finish.
 |
| Image by hackerheld |
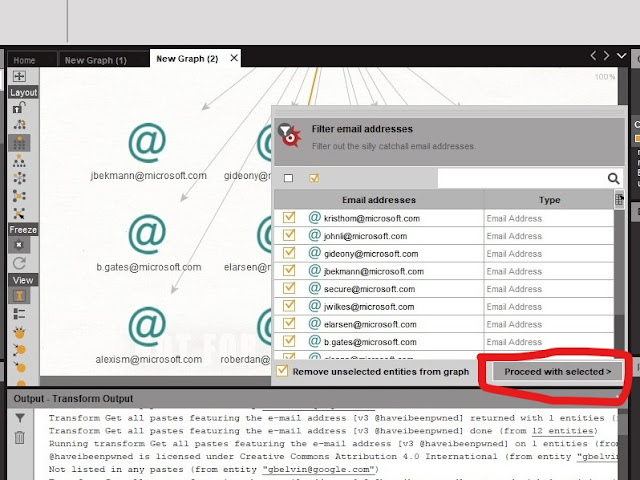
- After that, click on proceed with select.
 |
| Image by hackerheld |
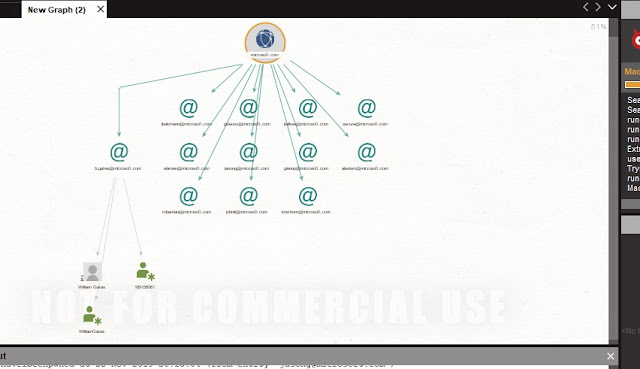
- Now you can see that data appear on the blank canvas. By double-clicking the entity you can add information or access the properties of the entity. This data contains e-mail, documents, persons identified, and other data that is on the domain in question.
 |
| Image by hackerheld |
- Then, select all the email addresses you found in the detail view pane. Right-click on it and type ‘have’ by typing this keyword you will get an option "Get all breaches of an email address" click on it.
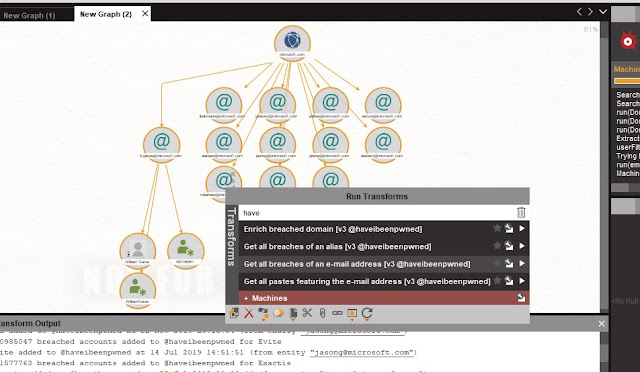 |
| Image by hackerheld |
- After that wait for a second, to see the results. It will uncover all breaches including the email addresses selected.
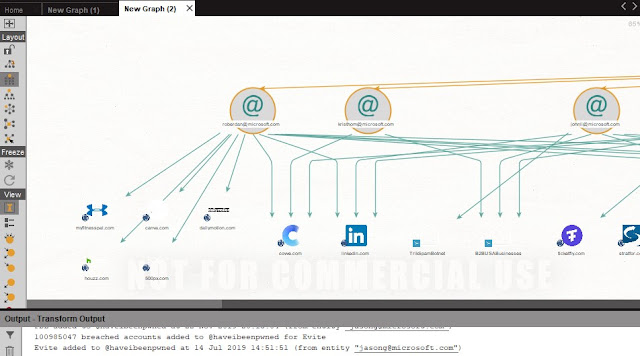 |
| Image by hackerheld |
- Then we try to discover what lost by who. To examine more information about the breaches the target employees were involved. Select any of this data breach, click on it and type "Enrich breached domain" then select it.
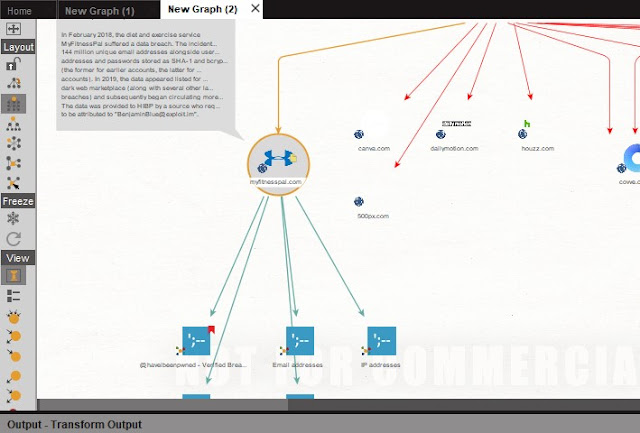 |
| Image by hackerheld |
- Now you see an expanded profile of information about each breach including elements to indicate whether passwords, usernames, or other types of data were lost. Additionally, with the specific date and short description of what was happened with the database breach.
Conclusion:- This article is all about find hacked email address using maltego. Feel free to ask in the comment section if you have any queries.












